# filter logs by date range
[acool@acool topsecret-host]$ git log --date=iso --pretty=format:"%ad %H - %an: %s" --after="2014-06-01" --until="2014-11-31" > commits-2014-06-to-2014-11.txt
//revert your working copy
git rm -r .
git checkout SHA1 .
//or (irreversible)
get reset --hard SHA1
//New repository(execute in project directory) (..I think git clone does this)
git init
//Listing, creating or deleting branches
git branch
//Changing branches
git checkout
//Committing changes
git commit
//Download remote repository
git clone
//Updating local repository
git pull //it fetches and merges remote repository with local repository (equals to: git fetch & git merge)
//Uploading local repository to remote repository
git push
//To see status and log entries run:
git status
git log
git log --stat SHA1
git log --name-status SHA1
git log -n 1 //last commit
//Workflow:
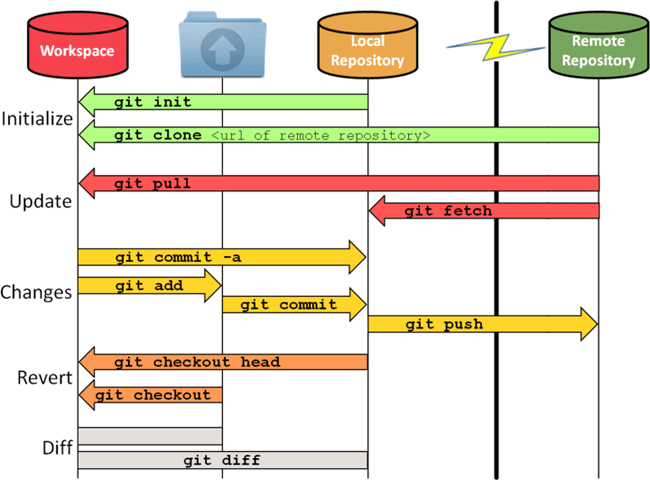
...another workflow example:
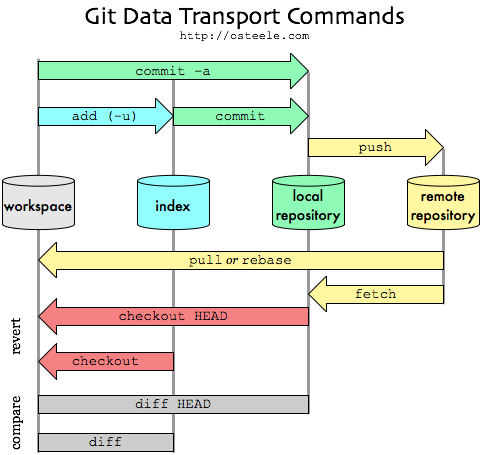
[ view entry ] ( 2241 views ) | print article
Switch(config)# no monitor session 1
Switch(config)# monitor session 1 source interface fastethernet0/1
Switch(config)# monitor session 1 destination interface fastethernet0/8
[ view entry ] ( 2924 views ) | print article
This tutorial demonstrates how to configure GRE over IPsec to connect two remote sites and to allow them to exchange routes dynamically with EIRGP.
http://www.angelcool.net/tutorials/cisc ... _EIGRP.pdf
[ view entry ] ( 2403 views ) | print article
//using tftpd32 server
rommon 36 > TFTP_SERVER=172.16.1.8
rommon 37 > tftpdnld
IP_ADDRESS: 172.16.1.33
IP_SUBNET_MASK: 255.255.255.0
DEFAULT_GATEWAY: 172.16.1.1
TFTP_SERVER: 172.16.1.8
TFTP_FILE: c1700-adventerprisek9-mz.124-7.bin
//If you want to boot from the image on the TFTP server without writing it to flash then use the command: tftpdnld -r
[ view entry ] ( 2225 views ) | print article
//problem:
ssh user@cisco_switch
//returns:
ssh_rsa_verify: RSA modulus too small: 512 < minimum 768 bits
key_verify failed for server_host_key
//solution (use SSHv1)
ssh -1 user@cisco_switch
/*...and if you have access to configuration mode enable larger RSA modulus in router. The modulus of the ssh RSA key pair on the switch/router is too small. If you have access, generate a new key pair on the switch/router with a larger modulus. */
crypto key generate rsa general-keys modulus 1024
..as always :)
[ view entry ] ( 1778 views ) | print article
//local network
//LAN IP addres 10.0.0.0 255.255.255.0
//R2(local router) public address: 23.0.1.0 255.255.255.0
crypto isakmp policy 1
authentication pre-share
exit
crypto isakmp key cisco address 56.2.11.2
//interesting traffic
access-list 100 permit 10.0.0.0 0.255.255.255 192.168.1.0 0.0.0.255
//transform set
crypto ipsec transform-set MYSET esp-sha-hmac esp-aes
//crypto map(bind all together)
crypto map MYMAP 1 ipsec-isakmp
set transform-set MYSET
set peer 56.2.11.2
match address 100
exit
//turn on policy (interface with public address)
int fa0/0
crypto map MYMAP
exit
===============================================================================
//remote network
//LAN IP address 192.168.1.0 255.255.255.0
//R4(local router) public address: 56.2.11.2
crypto isakmp policy 1
authentication pre-share
exit
crypto isakmp key cisco address 23.0.1.2
//interesting traffic
access-list 100 permit 192.168.1.0 0.0.0.255 10.0.0.0 0.255.255.255
//transform set
crypto ipsec transform-set OTHER_MYSET esp-sha-hmac esp-aes
//crypto map(bind all together)
crypto map MYMAP 1 ipsec-isakmp
set transform-set OTHER_MYSET
set peer 23.0.1.2
match address 100
exit
//turn on policy (interface with public address)
int fa0/0
crypto map OTHER_MYMAP
exit
//Now local hosts should be able to ping remote hosts
//verification commands
show crypto ipsec sa
/* IKE phase 1 tunnel is for private use when the two edge routers(R2 &R4) need to talk to each other,and it's used to create the IKE phase 2 tunnel (also called the IPSec tunnel).*/
: )
[ view entry ] ( 1910 views ) | print article
Lock-and-key access allows you to set up dynamic access lists that grant access per user to a specific source/destination host through a user authentication process(telnet login authentication).
See cut-through proxy, They call it like that in the ASA world.
[ view entry ] ( 2309 views ) | print article
The video demonstrates configuration of remote access IPSec VPN with Windows software client on Cisco router. We will look at both simple pre-shared key authentication as well as using client certificate. The client is placed behind a NAT router to demonstrate the significance of NAT Transparency, and compare it to raw IPSec and cTCP (IPSec over TCP). The video finishes off by showing how client can be allowed access to local subnet when a non-split tunnel is used.
Topic includes
- Easy VPN (EZVPN) with Software IPSec Client
- Client Pre-Shared Key and Certificate Authentication
- NAT Transparency (UDP 4500)
- cTCP aka IPSec over TCP
- 'include-local-lan' Option when not using Split Tunnel
[ view entry ] ( 2202 views ) | print article
vpnclient-winx64-msi-5.0.07.0290-k9.exe
https://supportforums.cisco.com/thread/2074141 (or built in software in Win7?)
"We sort of have two main categories of VPN. 1) Lan to Lan (aka Site to Site) and 2) Remote access. With lan to lan VPN's, there is some device (router, firewall, concentrator) that terminates bot ends of the connection. With Remote access, there is a piece of software installed on a PC/Laptop on one end and the other end would be terminated into a router, firewall or concentrator"
https://supportforums.cisco.com/thread/2074141
[ view entry ] ( 2140 views ) | print article
1.- The Factory
2.- The Singleton
3.- The Observer
4.- The Chain-of-Commands
5.- The Strategy
6.- The Adapter
7.- The Iterator
8.- The Decorator
9.- The Delagate
10.- The State
TO DO: Add a sample for each.
[ view entry ] ( 2041 views ) | print article
<<First <Back | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 | Next> Last>>
